Another quick snippet that I figured out this weekend. It’s not hard, but it’s something that I really wanted to do and had to look up where it was, so perhaps it will help you.
Problem statement:
I run a bunch of local services in my network. They aren’t exposed publicly (I use Wireguard to access them when out and about), so I really don’t need HTTPS. But (rightfully) a number of services behave better when they’re behind HTTPS + if there’s ever a service that’s running amuck (Internet of Things devices?) that’s listening, I don’t want them to see anything.
Options
Option 1: Use Nginx Proxy Manager to request certificates for each subdomain. It works quickly and well. Problem: All certificates are published to Certificate Transparency Logs. I don’t immediately mind exposing what I’m running… but I’d still rather now.
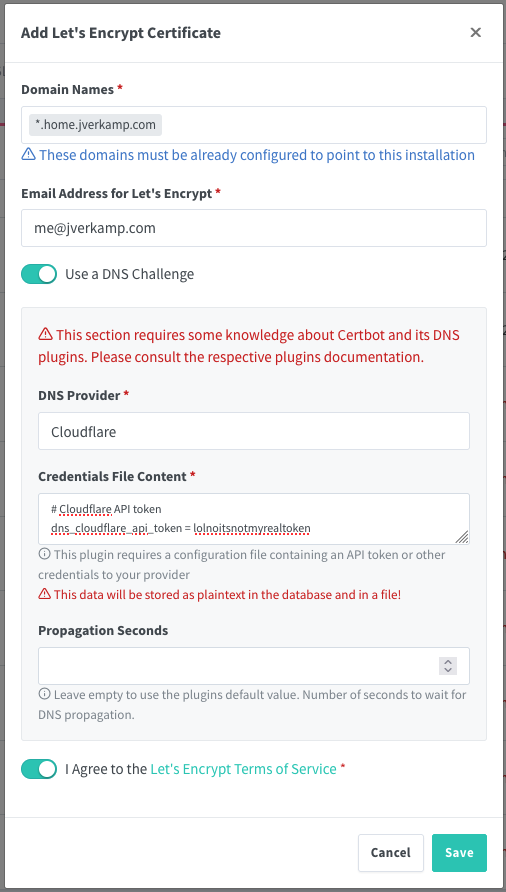
Option 2: Set up wildcard certificates. This requires integration with your DNS provider (since wildcards need a DNS challenge, not TCP).
Of course (based on the title), we’re going with option 2. 😄