Source: Chronal Coordinates
Part 1: Given a list of points, calculate the region of points closest to each point (using Manhattan distance). Return the size of the largest non-infinite region.
Part 1: Given a list of points, calculate the region of points closest to each point (using Manhattan distance). Return the size of the largest non-infinite region.
Part 1: Given a string, reduce it by removing pairs of letters that are the same letter but different cases. Repeat until you have a minimal string.
Part 1: Given a log of guard shifts and times asleep/awake, calculate the guard that was asleep most often and which minute they were most asleep for.
Part 1: Given a list of overlapping regions defined by (left, top, width, height) count how many integer points occur in more than one region.
Part 1: Given a list of strings, count how many contain exactly two of a letter (
a) and how many contain exactly three of a letter (b). Calculatea*b.
Part 1: Given a list of numbers (positive and negative) calculate the sum.
Let’s do it again! I’m starting a day late, but much better than last year 😄!
This time around, I’m hoping to solve each problem in both Python and Racket, both to show an example of how the languages differ and … well, because I can 😇.
EDIT 2018-12-05: Yeah… I’m not actually going to do these in both Racket and Python. The solutions are ending up being near direct translations. Since there are probably fewer people solving these in Racket, I’ll do that first and Python eventually™.
As always, these problems are wonderful to try to solve yourself. If you agree, stop reading now. This post isn’t going anywhere.
If you’d like to see the full form of any particular solution, you can do so on GitHub (including previous years and possibly some I haven’t written up yet): jpverkamp/advent-of-code
Quick post today. Let’s implement Tupper’s self-referential formula in Racket!
(tupper 960939379918958884971672962127852754715004339660129306651505519271702802395266424689642842174350718121267153782770623355993237280874144307891325963941337723487857735749823926629715517173716995165232890538221612403238855866184013235585136048828693337902491454229288667081096184496091705183454067827731551705405381627380967602565625016981482083418783163849115590225610003652351370343874461848378737238198224849863465033159410054974700593138339226497249461751545728366702369745461014655997933798537483143786841806593422227898388722980000748404719)
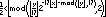
That’s the result of graphing the above function at a point rather far away from the origin. Specifically, where y is around that crazy big number. Look familiar?
In cryptography work, RC4 (Rivest Cipher 4) is well known as both one of the easiest to implement and fastest to run symmetric encryption algorithms. Unfortunately, over time there have been a number of attacks on RC4, both in poorly written protocols (such as in the case of WEP) or statistical attacks against the protocol itself.
Still, for how well it formed, it’s an amazingly simple algorithm, so I decided to try my hand at implementing it.
A quick programming post, since it’s been a while, inspired by this video:
I’m not going to go quite as far as that, but I thought it would be interesting to write up some quick code to generate portmanteaus1.